Securing your wireless LAN electronically and physically
Site surveys, correct use of built-in capabilities are crucial to safe information transport.
Wireless local area networks (WLANs) are providing in-office flexibility and convenience for roaming laptops, voice phones, or other portable devices. These characteristics, combined with standardization and aggressive cost reduction, foretell a future enterprise environment wherein the WLAN could prevail as the dominant client connection medium.
Commonly, the WLAN is installed as an overlay to the wired LAN. So, for network designers and installers, a new business opportunity is created: to provide the structured wiring to the WLAN access points (APs)-the data-communications equipment that interfaces with the wireless client adapter in the roaming device to the wired network via radio waves.
As popular as WLAN equipment has become, however, it has limitations. Concerns for network security-both the electronic information and the physical components-have become well publicized, and perhaps well founded.
The prevailing, standards-based WLAN products presumably are compliant with the Institute of Electrical and Electronics Engineers (IEEE; www.ieee.org) 802.11b, 802.11a, or 802.11g standards. The standard defines how the radios in the AP and wireless client device will communicate with each other. The standard also describes the basic communication protocol that permits devices to share the common medium-the airwaves-similar to the manner in which the IEEE 802.3 Ethernet standard describes how devices can share a twisted-pair wire.
The label “Wi-Fi compliant” on a product indicates that the product has been subjected to 802.11b, 802.11a, and 802.11g interoperability tests. Any Wi-Fi-compliant client device should be interoperable with any other Wi-Fi-labeled AP or client device.
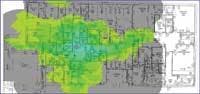
Given that the network is no longer constrained to hosts connected by data wires, and that usable radio signal strengths can be measured a kilometer away from the AP or wireless client adapter, how can the wireless network provide reliable coverage where coverage is required, and minimize emissions outside of the coverage area?
Two kinds of security
The first requirement is for electronic security. The standards define, and compliant equipment supports, methods to authenticate client adapters and to encrypt the data payload to provide access and information security. Authentication is the process of verifying that the client attempting to engage the network is authorized to do so. Effective encryption will prevent an eavesdropper from using the transmitted information.
The second requirement is to provide physical security of the WLAN components, which involves mounting the APs in such a way that they cannot be stolen, moved, vandalized, blocked, or damaged. It also involves considering coverage areas, and minimizing coverage outside of the area intended for coverage. For example, maybe you would like your coverage to include the building interior, but perhaps not the parking lot, adjacent buildings, or public hallways. Such coverage specificity requires a radio-frequency (RF) facilities analysis, structured AP placement and wiring, and antenna-pattern selection.
Pay now, or much more later
Electronic security is a matter of degrees, and the highest network security generally comes at the highest initial cost. Remember, however, an inadequate security solution could be very costly in terms of network downtime or inadequately protected enterprise communications and information. A number of electronic-security solutions are available for WLANs, but they may not all be interoperable. Different organizations will have different requirements for electronic security, so it’s worth spending the time to understand the target organization’s requirements and capabilities. A comprehensive review of security solutions is beyond the scope of this article, but some of the important definitions are provided here.
The IEEE 802.1x standard describes wireline authentication, authorization, accounting, and encryption with a Layer 2 extension for WLANs, enabling a security level on par with most wired networks. 802.1x describes the following:
• The Extensible Authentication Protocol (EAP) provides authentication between the client and the authentication server. Several EAP types are available, including EAP-Cisco, EAP-TLS (EAP Transport Layer Security), EAP-TTLS (EAP Tunneled Transport Layer Security), and PEAP (Protected EAP); these let an enterprise choose the authentication type that best suits its needs.
• Encryption is at the link layer between the WLAN client and the AP. The current encryption mechanisms available are Wired Equivalency Privacy (WEP) and WEP plus TKIP (Temporary Key Integrity Protocol), Wi-Fi Protected Access (WPA), and Advanced Encryption Standard (AES). The emerging IEEE 802.11i standard for encryption prescribes AES.
• Authorization is controlled by the virtual LAN (VLAN) membership in combination with the access controls applied at the access router terminating the VLAN.
• RADIUS (Remote Authentication Dial In User Service) provides the accounting, via communication between a RADIUS server and the APs.
In addition to understanding these authentication and encryption issues, it is recommended that wireless LANs be a separate LAN segment from the wired network. It may also be appropriate to engage a wireless intrusion-detection system (WIDS), which generally comprises WIDS sensors distributed throughout the facility, and an IDS server or appliance. The IDS server or appliance aggregates detected radio packets and is able to report unauthorized APs, unauthorized wireless clients, malicious behavior, and malfunctions in APs or clients. Users should review their network security policies and periodically audit their facilities for rogue wireless networks or intrusion attempts. Network managers can program WIDS to enforce these policies. Finally, the APs’ transmit power should be adjusted to provide RF coverage only where desired, and minimize RF outside the zone of intended coverage.
Physical security
In addition to electronic security, network designers, installers, and users should incorporate physical security for APs. The AP locations will be based on the results of an RF site survey or facilities analysis. This site survey is essential for providing effective RF coverage when more than one room is involved, and generally is much more cost-effective than guessing AP quantity and location.
Because the APs are required to provide RF coverage, they inherently cannot be locked into a telecom facility. The APs, however, by their nature require exposure to provide RF coverage, and must be protected from theft, accidental moves, vandalism, damage, or blockage. These requirements often are at odds with each other, so network managers must provide physical security for APs in-situ.
For the sake of convenience, the AP is sometimes placed above the drop ceiling in the plenum space. This approach, however, is less than ideal. The drop ceiling may introduce 2 to 3 decibels (dB) of attenuation between the AP and the area intended to be covered, which results in a 30% reduction in coverage range and a 50% reduction in coverage area. Therefore, the AP can be placed in the plenum space only if the RF site survey was performed with the AP in the plenum space. Significantly more APs may be required within the facility to provide desired coverage if the APs are mounted above the drop ceiling, versus below the drop ceiling.
If installed in the plenum space, the AP must be plenum-rated and must be installed per the National Electrical Code specifications for plenum-space installations. Additionally, maintaining the AP may be more difficult within the plenum space, and even locating the AP may be a problem.
Ideally, the AP should be mounted in an AP enclosure that can be locked and that facilitates antenna connection. External antennas can be connected to the AP via short coaxial jumper cables, integrated directly with the enclosure, or protruding through the enclosure from the AP. In any case, the antennas should emulate the antennas used in the RF site survey.
Enclosures deter theft, vandalism, and accidental moves, and they are less likely to be accidentally blocked than a standalone AP. Integrated antennas prevent tampering and theft. The enclosures also support moves, adds, and changes (MACs). As AP standards or requirements change, the AP can be swapped out of the enclosure, or additional APs can be added, leaving the data wiring and line wiring in place.
Generally, due to attenuation concerns, it is good to avoid radiating through plastic or fiberglass enclosures. Also, plastic or fiberglass enclosures may not be acceptable in plenum spaces.
Antenna selection
Using the correct antenna can optimize RF coverage, which means not only providing RF signals to the wireless client device, but also minimizing interference between APs, maximizing data throughput, and minimizing the number of APs used. Most AP manufacturers provide products with detachable antennas to meet a variety of WLAN design needs. For wall-mounted APs, it’s wise to choose a directional panel antenna that radiates into the room. For APs mounted near the center of a room, choose an omnidirectional antenna.
In years past, a WLAN designer was constrained to use the AP manufacturer’s antenna-and for 802.11a WLANs, which operate in the 5-GHz band, only APs with non-detachable antennas could be used. In July 2004, however, the Federal Communications Commission (FCC) changed some of its rules regarding the use of external antennas with APs, giving WLAN installers more flexibility in network design for RF coverage. According to FCC rule change CFR 47, Section 15.204, paragraph (c)(4), you can use any antenna that is of similar type to the antenna provided by the manufacturer, with equivalent or lower directional gain. Also, 5-GHz 802.11a APs with detachable antennas are now permitted, thereby providing you with greater flexibility when using external antennas in 802.11a-compliant networks.
Checklist for now and the future
In summary:
• When using WLAN equipment, engage the standards-based authentication and encryption available with Wi-Fi-compliant client adapters and APs.
• Remember that the equipment may be shipped with authentication and encryption disabled.
• Review security policies and isolate the WLAN from the wired network.
• APs are critical to WLAN performance, so it is necessary to physically secure them to avoid network downtime and loss of capital equipment.
• Understand the RF site survey, and install the APs so they provide optimum RF coverage while mitigating mutual interference.
• Use an antenna that is suitable for the area to be covered, and perform an RF site survey with the same type of antenna.
Wireless LAN standards are evolving, so anticipate upgrades, either through firmware or hardware, in the near future. Structure your WLAN design for future performance enhancements and MACs.
SCOTT D. THOMPSON is director of engineering for Oberon (www.oberonwireless.com).