In the more than two years following the September 11 attacks, changes in the security market have been astounding. Widespread fear, terrorist threats, war, and government reform have created an overwhelming demand for security solutions in physical and IT security. As a result, the entire security industry has experienced increased spending, enhanced technologies, and expanded professional security services.
The past six issues of Cabling Installation & Maintenance have covered a variety of security topics ranging from campus IT and alarm systems to biometrics and video surveillance. As we move into 2004 and beyond, experts and analysts examine current drivers in the security market, identify the need for a more integrated approach, and recognize the obstacles along the way.
Protecting physical places
Surveillance, biometrics/access control, and hazard detection are the main components of the physical security market, which according to some experts is partly being driven by the U.S. legal system. "Premises liability and negligence lawsuits are partly responsible for driving the physical security market right now," says Dr. Randall Atlas of Miami-based Counter Terror Design, Inc. (www.cpted-security.com). "Unfortunately, lack of funding in this poor economy is stifling many efforts to properly implement solutions."
Atlas says that although the cost of products has come down due to cheaper technology and manufacturing processes, many companies are not properly integrating technologies. "They throw money at state-of-the art cameras, but watch the wrong thing. There's not enough funding for the professional services that can properly analyze what needs to be watched, why it needs to be watched, who should watch it, and who should respond," says Atlas.
Despite lack of funding for proper implementation, the technology behind physical security components continues to evolve. Surveillance—such as CCTV, sonar, x-ray technology, and listening devices—is the fundamental component of physical security, with a long history of deployment and an experienced user base. Surveillance technology is currently being driven by the demand for increased flexibility, ruggedness, and decreased cost.
null
A 2002 Remote Video market report from JP Freeman Co. (www.jpfreeman.com) predicted that the video surveillance market will continue to rise as the Internet plays more of a role in surveillance and camera technology comes down in price. This trend is supported by the many digital recorders now on the market that are more easily integrated into existing networks. According to the Freeman report, smarter systems are on the rise with desired features like object tracking, a motion-sensitive recording and tracking capability that follows a moving object out of one camera's range and activates the next camera.
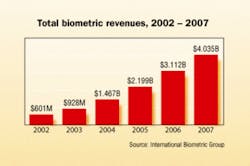
Biometric access control systems include fingerprinting, hand geometry, facial recognition, voice recognition, iris scans, and signature verification. According to a recent market report by International Biometric Group (www.biometricgroup.com), global biometric revenues are expected to reach more than $4 billion by 2007, up from $6 million in 2002. The report states that increased revenues will be driven mainly by "large-scale public biometric deployment and the adoption of standardized biometric infrastructures and data formats."
According to the report, fingerprint technology is projected to account for the majority of the biometric market share due to the wide range of applications with which it effectively operates. The report also states that the government sector will be the leading biometric vertical market through 2007, followed by the financial sector, then travel and transportation. "The various scenarios in which government agencies must identify and authenticate both citizens and employees, particularly subsequent to 9/11, is a critical growth factor," says International Biometric Group.
null
Hazard detection, such as sensors and detectors for biological and chemical agents, is a crucial component of the security industry. Events like the postal anthrax attack and other possible terrorist threats are the main drivers for this segment of the market. According to Sensor Business Digest, nanotechnology-based sensors are expected to surface in the marketplace significantly in the next ten years. Nanotechnology is based on microscopes with atomic resolution that can examine atoms and molecules, allowing for sensitive, selective, and responsive sensors that can quickly and accurately detect chemical or biological agents.
"Nanotechnology-based sensors will increase, because they are smaller, higher performing, and less expensive than conventional sensors," says Sensor Business Digest. "Further efforts will be required to develop nanosensors based on advanced materials that can be readily manufactured in high volume.
Securing cyberspace
The need for IT security continues to grow as businesses increase partnerships across the world. "Any big business today has a lot of partner links and WAN connections caused by practices such as outsourcing to Europe and Asia," says Michael Rasmussen, CISSP, a Giga analyst covering information protection. "The dilemma is that as we increase business partnerships, security goes downhill. At the same time, companies are being tasked with making sure they have more IT security."
In the past, most network security solutions included mainly firewalls and authentication to prevent intrusion, and antivirus software to maintain system reliability. According to recent research and analysis from the Yankee Group (www.yankeegroup.com) and Gartner (www.gartner.com), however, IT security is transitioning from passive intrusion detection systems (IDS) to active intrusion prevention systems (IPS).
"The explosive growth in public-protocol Internet use has yielded far more traffic than IT security, as it stands, can handle," says analyst Eric Ogren of Yankee Group. "With increased traffic, additional IT staff are required to interpret IDS reports and simplify rules, which is why many are now looking at IPS technology to maintain network availability."
Analyst John Pescatore of Gartner reports that both IDS and IPS should be used simultaneously through 2006 to meet best security practices. According to Pescatore, a true IPS must meet three key criteria: It must not disrupt normal network operations, it must block malicious actions using multiple algorithms, and it must know the difference between attack events and normal events. "As processing power and security algorithms performance increases, true intrusion prevention will grow in importance," says Pescatore.
The IT security market is driven by many external factors and regulations," says Rasmussen. "There are mandates requiring institutions to implement IT security. We have regulations from the federal reserve, HIPPAA compliance to guarantee security and privacy of health information, the Gramm-Leach-Bliley Act that protects personal financial information, and the California Senate Bill 1386 that mandates anyone with customers in California must disclose any breach of security to their records."
According to Rasmussen, we will see many more regulations in 2004 and beyond that will continue drive the IT security market.
Taking a holistic approach
Regardless of trends and developments in physical and IT security technologies, security professionals agree that the industry must move toward integration from an operational and technology standpoint. Increased awareness followed by professional risk assessment to determine vulnerability will help the market move toward that integration. "When those assessments come in, professionals then need to develop a functional security system design based on mechanical, technological, organizational, and natural solutions," says Atlas. "The integration of all of these is key to a holistic security system, and someone needs to pull it all together."
Many companies are starting to see the need for that "someone" to pull it all together. "Having a security officer responsible for physical security and an information officer responsible for IT security is a big problem," says Rasmussen. "The two can no longer be managed as silos, and we need a higher level to bring things together." According to Rasmussen, over the next five years, many organizations will be moving towards the implementation of a chief risk officer position. "The chief risk officer is a true executive that reports to the board and is responsible for managing operational risk and all of the components beneath that—physical security, IT security, insurance, audit, compliance, privacy issues, contingency planning, and disaster recovery."
Security technologies must also be integrated by means of interoperability and standards. In a recent article of the on-line BiometriTech (www.biometritech.com), John Carty of General Defense Systems, Inc. stated that for any security system to properly function, security solutions require integration among operating systems, system services, databases, and applications. "Imagine a facial recognition system receiving poorly illuminated images from out-of-date cameras; or an image storage system improperly integrated with system security," writes Carty. According to Carty, vendors should consider the key drivers in the integrated security solutions marketplace as they move to deliver solutions, including integrated components, higher volumes of data storage and throughput, cooperative systems, ease of use, and reliability.
According to Rasmussen, several efforts are underway to accomplish product interoperability and standard operational procedures. Many of these efforts overlap. For example, the BioAPI Consortium (www.bioapi.org) develops application programming interfaces for various biometric technologies, ISO 13335 gives guidance on IT security management, and the detailed ISO 17799 includes security risk assessment as a basic requirement. "We're tracking over 450 IT security vendors, and the reality is that organizations don't want to deploy 450 band aids," says Rasmussen. "The security needs to be built into the operating systems, into the applications, and into the network."
Getting priorities straight
While security is far better than it was on the eve of 9/11, industry professionals believe that we still have a long way to go. "We were nervous in the months following the September 11 attacks, but the initial shock wore off, " says Atlas of Counter Terror Design. "The attitude of 'it can't happen here' still exists in many areas of the country." Atlas believes that security in the big scheme of things is still a lower priority than it should be. "There are universities that have known about security threats for years, but they still put their money into athletic facilities," says Atlas. "When we have our next big terrorist event, and going to the mall becomes a life threatening experience, priorities will shift."
Although the security market has survived the economic downturn better than others have, lack of funding continues to hinder growth. "The pressure is on for chief security officers to justify their budgets," says Rasmussen. "If they say they need security, they need to be able to translate in dollars why and what the business impact is. This is where the role of the chief risk officer comes in."
While security includes many components that need to come together, Atlas says it needs to start with each one of us at a grassroots level. "If everyone took the time to look at their house, their office building, their parks, and their schools, the level of vulnerability to crime and terrorism would be decreased one house, one block, one neighborhood, and one city at time," says Atlas.
Betsy Ziobron is a freelance writer covering the cabling industry, and a regular contributor to Cabling Installation & Maintenance.