Choices of media, connectivity, and personnel all factor into your network's level of security.
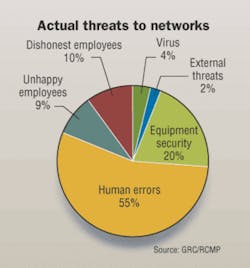
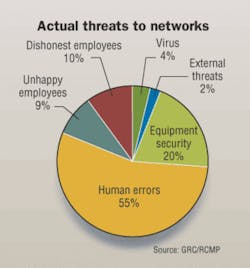
In recent years, we have seen the networks of some of our most respected and powerful agencies and banks breached, often by company insiders. Information technology and network decision-makers are tuning in to this important buzz, as security affects all layers of their network. We have come to realize that security is everyone's business, and that it is a never-ending task with no room for blind spots.
The United States government, of course, is taking security seriously, most visibly evident by the establishment of the Department of Homeland Security (DHS). The DHS' strategy focuses on six critical mission areas: intelligence and warning, border and transportations security, domestic counterterrorism, protecting critical infrastructure, defending against catastrophic terrorism, and emergency preparedness and response.
As per the DHS, the critical infrastructure consists of all sectors that provide essential goods and services that people need to survive, such as food, water, public health, government operations, telecommunications, banking, energy, postal service, and emergency services. Each sector is required to evaluate the level of security needed, and to elaborate a security and disaster-recovery plan. It is important that these plans include a method of protecting the LAN and its physical infrastructure, since these are the physical pathways required to transfer vital data, voice, and images.
Beyond this DHS initiative are problems that LAN managers may encounter more frequently—network tampering or failure resulting in costly downtime. Cameras, access-control systems, intrusion-detection systems, and a multitude of other powerful tools may be used to increase the security of the enterprise and of its information network. Most of these products, however, do not always protect the enterprise against the "internal threat." And as numerous studies show, most security breaches come from perpetrators within the LAN.
As for the physical infrastructure supporting the LAN, most IT managers are keeping it locked. But is that enough? Perhaps for some of the most secure and isolated networks in which access is strictly controlled and everyone working in the IT room has been carefully cleared. But this level of protection is not in place for most of today's installations.
Take necessary steps
The first step toward securing a network is to define the targeted level of security based on the perceived threat level and its consequences. Once the desired level of security is defined, you must take it into account at every step of the network—design, implementation, and operation.
For structured cabling infrastructure, the most important decisions will be made during the planning and design phases . Component selection and the choice of partners will play an integral role in the realization of the targeted security level.
At the network-design level, one of the first choices you'll face is the media for the cabling system: copper or fiber? A secure network can be designed with either media; both feature different strengths in the security equation. The criteria that should be used when comparing the two media are data throughput required, security that can be achieved with the media, specific project needs, and cost.
Copper solutions
If your objective is to prevent accidental access or restrict access to authorized personnel, a copper infrastructure is a cost-effective choice. By selecting the right products and using them in a design in which security features are implemented, you can build a copper-based cabling infrastructure that will optimize your security plan.
To reduce the possibility of accidental access or intrusion, the policy of color-coding services can be an effective method of stopping unauthorized people from disconnecting or moving a part of the critical physical infrastructure. This policy is often integrated for fire-alarm services.
Also, security features are often built in to certain components. For example, an insulation-displacement connection (IDC) cross-connect system is an ideal candidate for providing a secure installation that has a specific need for redundancy, manageability, and robustness. Redundancy can be achieved efficiently because the system offers high density, can be wall-mounted, and only costs a fraction of the price of a modular patch-panel system.
Secure manageability is one of the biggest features of the IDC system. The use of cross-connect wire or specific patch cords allows all patching to be centralized on a wall. Well-identified distribution and equipment fields will prevent patching mistakes. Access for making changes on the patching fields can be controlled by using locking covers, special service guards (to protect individual pairs), or by controlling access to the punchdown tools.
Fiber solutions
While generally more expensive than copper solutions due to the cost of electronics, fiber solutions have several advantages over copper in the security arena. Although tapping into a fiber system is not impossible, it is not easily accomplished either. Tapping into fiber is easily detectable by the significant power loss of the light signal that results from an intrusion, and such loss events can be monitored to provide maximum security. For networks requiring a high level of security, a solution like a fiber-to-the-desk infrastructure and fiber backbones will optimize the security plan.
Another advantage of a fiber network is the possibility of concentrating all the active equipment within the same telecommunications room by following a centralized fiber topology. Concentrating all active equipment in the same room facilitates access control and monitoring. The purpose of Annex A of ANSI/TIA/EIA-568B.1 Centralized Optical Fiber Cabling is to assist in the planning of a multimode fiber-to-the-desk cabling system using centralized electronics versus the traditional method of distributing the electronics to individual floors.
Centralized electronics using the centralized fiber cabling topology allows for longer runs and reduces the number of telecommunications rooms, thus limiting the number of potential intrusion points.
One way to control access to a secure site is to maintain the cabling infrastructure using local employees. A preterminated fiber system does not require specific fiber expertise, and is quick and easy to deploy and maintain with local personnel. It allows for a quick turnaround in case of emergency. Fiber-connection density is also crucial in secure installations, where a lot of fiber terminations are used. Preterminated solutions are readily available on the market today, including NORDX's FiberExpress Bar and Preterminated FiberExpress Manager Modules.
Access to the cabling and network systems should be limited to authorized personnel only and be rigorously controlled. All spaces such as telecommunications rooms should be locked to protect against intrusions and monitored by the security system for access control. Cabling should be routed through pathways and spaces that are not accessible by the public or by other tenants. Conduits or closed raceways can be used to limit access to the telecommunications cabling in pathways, and also provide security when a special mechanical protection is required and/or the telecommunications cabling is going through public and accessible spaces.
Redundancy and partnerships
To reduce network vulnerability, you must develop a disaster recovery plan. One of the best ways is to add redundancy to the network infrastructure. Redundancy will increase the network's reliability and contribute to the elimination of a possible single point of failure. The redundancy design should take into consideration the active network as well as the telecommunications cabling infrastructure.
Once you've selected passive components and structured cabling (fiber and copper), intelligent cable management systems can be used to protect the physical network. Systems of this type allow an IT manager to monitor in real time the enterprise physical network. Such technologies allow rapid detection and response.
For high-level security needs, the choice of key people and partnerships will make a difference in the quality of the products, installation, and maintenance of your network. An experienced and qualified team along with the best cabling products on the market, proper cabling design, quality installation, and good administration will translate to high performance, quick turnaround, and a higher level of security.
Andre Mouton and Benoit Chevarie are product line managers with NORDX/CDT (www.nordx.com). Julie Roy, RCDD/LAN Specialist, is IBDN systems, applications, and standards manager with NORDX/CDT.