Two-way solution for wireless LAN security
Addressing both physical security and logical security will help ensure your wireless communications are carried out safely.
With centralizedwireless networking becoming more ubiquitous, security is becoming a major focus for customers. When I meet with them, the first comment is often, “What is your wireless security solution?”
Enterprise customers already understand the need for wireless access, but are really concerned with the security aspect of Wi-Fi. The best way to answer that question is to describe the security solution in two parts: the physical layer and the logical layer. In this article, we will explore security for a centralized wireless network.
Physical security
When discussing physical security, several questions must be answered, including, “Are your access points secure?” and “Is your centralized controller secure?” Let’s examine these individually.
• Access-point security. One of the biggest issues with the physical security of wireless networks is access point theft. Due to the nature of access point deployments (usually in open, unsecured, common areas), access points can disappear. The best way to combat this issue is to select access points that integrate into your existing structured cabling infrastructure. If the access points look like other common items, they are less likely to be a target of theft.
• Centralized controller security. With a centralized wireless local area network (LAN), the “brains” of the network are centralized in the server-like appliance called a controller. While most controllers have advanced software security embedded to combat hacking, an often-overlooked issue is the controller being stolen. Most enterprises look at wireless networks as non-mission-critical; it’s perceived they do not need the same level of physical protection as a wired network. This could not be further from the truth. Controllers should be located in the same physical location as other networking equipment-in a secured environment.
Logical security
Logical (software-based) security is equally important. The best way to discuss logical security is to understand the basic pillars (authentication, encryption, authorization, and intrusion protection) of any centralized wireless security solution:
• Authentication. User identity is important on a wireless network. Because there are not any physical ports, it is essential to ensure that only authorized users are allowed access. For auditing and accounting purposes, it is recommended that WPA or WPA2 (defined and further discussed later in this article) be used with 802.1x and a Remote Authentication Dial-In User Service (RADIUS) server. A RADIUS server allows wireless users to be authenticated against backend user databases, such as Microsoft Active Directory, Novell Netware, and LDAP. This provides a sign-on experience for users that is similar to their wired network login. For even higher levels of authentication, most solutions support smart card or token-based authentication, such as SecureID.
• Encryption. A primary concern of wireless is that anyone with a network card can gain access and capture packets with a wireless sniffer. The original 802.11 standard developed Wired Equivalent Privacy (WEP) as a way of encrypting traffic at Layer 2, but most of us have heard the news that WEP is not secure. The answer for many years was to use a virtual private network (VPN) to provide data protection across wireless networks. While this provided strong encryption, it also added a lot of overhead, thereby decreasing throughput. A better way to encrypt traffic is via a Wi-Fi Protected Access (WPA), which uses the Temporal Key Integrity Protocol (TKIP) and dynamic key rotation, making it difficult to capture and decipher the data.
For higher security needs, Wi-Fi Protected Access v2 (WPA2) is based on the 802.11i standard that uses the government-rated Advanced Encryption Standard (AES). WPA2 operates in a similar manner as WPA, but with much higher levels of encryption. In most cases, older client devices may not support WPA2 due to the processing needs required to perform encryption with AES. It’s also important to look for centralized solutions that encrypt and decrypt data at the wireless controller. This way, traffic is protected from the client station all the way to the wireless controller and not decrypted at the access point.
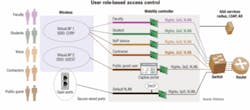
• Role-based authorization. Placing users and devices into roles that have secure access policies is a key feature that only some solutions support via an integrated stateful firewall, which keeps track of the state of network connections traveling through it. (See “Layers 4 through 7”.) Firewall integration into the wireless controller allows for secure separation between the wireless and wired network as well as between individual wireless devices. In a university environment, roles can be created for different types of access, such as student, faculty, guest, and printer. Students may have access to the residence hall networks and certain areas of the school network, while faculty have complete access to the school network but are protected from the residence hall networks. Additionally, printers in classrooms may only be able to use WEP, giving them access only to the specific port level of the print server, even if compromised. Through the use of a stateful firewall, you have multi-layered protection for Layers 3 through 7 of the OSI model.
• Intrusion protection. An intrusion detection system (IDS) is another added feature to bolster the security of any wireless deployment. Wireless networks are susceptible to typical wired LAN attacks as well as to their own unique types of attacks, requiring an IDS be built specifically for them.
Rogue access points are a common intrusion type that can erode the highest levels of security in any organization. All it takes is for someone to install an unsecured access point on your network to leave you vulnerable. Wireless controllers typically have the ability to detect and prevent this and other types of intrusions, or alert administrators to their existence. Some controllers prevent wireless clients from attaching to rogue access points by creating a denial of service (DoS) attack against an unauthorized access point.
Many centralized wireless deployments can program access points to monitor the air. In this type of scenario, the job of the air monitors is to constantly scan all 802.11a/b/g channels for IDS signatures that match a known attack type. Once an attack is identified, the wireless controller can take action to prevent or notify of network intrusions, such as passive and active probing, wireless bridge detection, detection of common attack tools (such as Asleap and Airjack), man-in-the-middle detection and prevention, and client impersonation.
Security implementation
The most challenging part of understanding wireless security technologies is determining where and how to best implement them. The easiest way to remember where to implement these technologies is to correlate them to a position on the OSI stack. Here is an easy-to-remember list.