Biometrics technology putting a face on security
by Patrick McLaughlin and Steve Smith
A round-up of some of the latest biometrics products and systems, as displayed at ISC West 2007.
Technologies and products based on biometrics-facial and hand recognition-were on full display at the ISC West exposition, held in late March. In fact, one of three specialized pavilions within the exhibition focused on Access Control/Biometrics; the other two pavilions were labeled IP Security and Video Surveillance.
The Access Control/Biometrics pavilion included more than 80 companies, many of which displayed a full breadth of products. The majority of those exhibiting focused on forms of access control other than biometrics systems; however, those that did display their biometrics wares had some of the latest technology in that arena.
This month, we bring you some of the latest biometrics products and systems, as they were displayed at ISC West 2007. (More information on the exhibition, its participants, and the accompanying educational sessions can be found at: www.isc365.com.)
Facial recognition tools deliver in real time
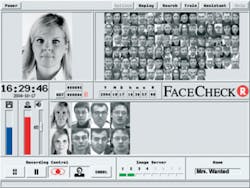
Designed for biometric identity checks, video observation, access monitoring and other security installations requiring facial recognition and recording, the FaceSnap recorder combines a digital video recorder (DVR) with facial recognition software to locate and extract images from video footage. Individual facial patterns can then be recorded and stored in what the company says is an easy-to-navigate database that can be viewed on a computer, or used as a back-up to existing security systems. A key feature of FaceSnap is its ability to recognize and record facial images from various viewing angles. If multiple faces enter its field of vision, FaceSnap automatically records all of them. The recorder system comes complete with video inputs for all standard formats, plus a 10/100 Mbits/sec Ethernet network interface, with remote access available via a standard network connection.
FaceCheck server, a real-time facial identification software system, operates on a FaceSnap recorder platform, connecting to one or several FaceSnap imaging units in a TCP/IP network. FaceCheck maintains one or several “watch lists,” which contain portrait samples of identified persons. Each received image is compared against all of the portrait images in the selected “watch lists,” and when an incoming image matches one of the portraits, an alert appears. A typical alert shows the face that triggered the alert and the corresponding photo from the “watch list” so that the operator can visually verify the system alert. One FaceCheck server can be connected with up to eight FaceSnap imaging units (more connections available on request).
CROSS MATCH TECHNOLOGIES
www.crossmatch.com
3D face reader performs in daylight or darkness
The VisionAccess 3D face reader is comprised of a real-time 3D surface scanner working in invisible near-infrared light, and is designed for quick positioning and rapid authentication in less than one second. Suitable for both identification and verification in such security installations as corporate buildings, banks, hospitals, airports, and any commercial or civil entry point, the VisionAccess system can be used as a stand-alone system or interfaced with legacy access systems in a distributed network. Features include rapid, real-time matching and recognition, equal recognition performance in light or complete darkness, user-defined authentication settings, and biometrics/card/PIN that can be used in any combination for single, dual, or triple factor authentication.
BIOSCRYPT
www.bioscrypt.com
Space-saving embedded IRIS authentication technology
Iris authentication is considered the fastest, most accurate, and scalable of all biometrics technologies, but until recently has also been considered too expensive and too equipment-dependent for widespread use. In contrast to comparable iris-based authentication technologies that require significant computing power and connection to a server, the Irikon system security module, stand-alone door lock, and flash memory features embedded iris technology in one chip or module, and operates on a platform independent of servers or other computer devices. The Irikon security module (right), designed to protect system log-on access from authorized users for notebook PCs, mobile PCs, and PDAs, enables the devices to be activated after the iris identification process so that the data within the device can be protected. A security utility pops up before operating systems (such as Windows) read into the system, meaning the devices can be protected by the highest level of security.
The stand-alone door lock (top right),designed for residential and small office, does not need to be connected to a computer or power source since it is powered by its own embedded microprocessor and internal batteries. Irikon flash memory, says the company, is the world’s first to implement iris authentication, and ensures that confidential data is secured. Only a pre-registered user can access the data within the flash memory. Users do not need to recall passwords but rather look into the iris camera on the flash memory to activate.
REHOBOTH TECH
www.rehobothtech.com
Enhanced fingerprint ID eliminates password resets
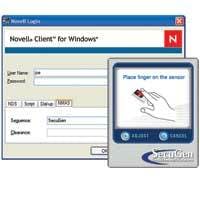
Version 2.2 of the SecuGen Enterprise NMAS Login Method software now features improved system-wide security threshold and individual user security threshold, a diagnostic tool that determines if a user’s fingerprint data already exists in the directory, an option for administrators to have users self-register their fingerprints, and reduced administrative overhead caused by password resets. In partnership with Novell, the SecuGen NMAS (Novell Modular Authentication Service) method works with an organization’s existing Novell infrastructure, letting users authenticate to eDirectory with their fingerprints. “A great advantage of using fingerprints is that an organization can be sure their users are who they say they are, especially when trying to access sensitive or vulnerable resources,”
SECUGEN CORP.
www.secugen.com
PATRICK McLAUGHLIN is chief editor and STEVE SMITH is executive editor of Cabling Installation & Maintenance.