Designing and building a safe and secure WLAN
Wireless Local Area Networks (WLANs) have become popular, providing in-office flexibility and convenience for roaming laptops or other portable devices that remain connected to the LAN.
Combined with standardization and aggressive cost reduction, WLAN is poised to prevail as the enterprise's dominant client connection medium. For network designers and installers, opportunities abound to provide the structured wiring for the access points—the data communication equipment (DCE) that links the wireless client adaptor in the roaming device to the wired network. This is a new business opportunity above and beyond traditional network design and installation.
But as popular as WLAN has become, there are several red flags that you need to heed when designing or installing. Specifically, concerns for network security—when the network is augmented with the wireless component—have become serious and well publicized.
The prevalent WLAN equipment, commonly called Wi-Fi, actually means the equipment is compliant with the Institute for Electrical and Electronic Engineers (IEEE) 802.11b standard. This guideline defines how the radios in the access point and wireless client adaptors will communicate with each other. The standard also describes the basic communication protocol that permits devices to share the common medium—the airwaves. This is similar to the manner in which the 802.3 Ethernet standard describes how devices can share a wireline.
Given that the network is no longer constrained to hosts connected by data wires, and that usable radio signal strengths can actually be measured a kilometer away from the access point or wireless client adaptor, how can a WLAN installation be protected from intrusion?
The first red flag to address is electronic security. The 802.11b standard defines—and compliant equipment supports—methods to authenticate client adaptors and to encrypt the data payload for providing access and information security.
null
Authentication is the process of verifying that the client attempting to engage the network is authorized to do so. Unfortunately, the 802.11b authentication process has proven to be inadequate for most enterprise applications, as it is possible for unauthorized client intruders to "authenticate" themselves by studying access point transmissions, and emulating an authorized client.
The encryption protocol is called Wired Equivalent Privacy (WEP), which is intended to provide roughly the equivalent security of the wired network over the WLAN by encrypting the data payload. But WEP is not a particularly strong security measure either, and once an intruder authenticates, downloadable shareware allows WEP penetration. Even worse, many WLAN users do not even engage the WEP protocol, opening the door to even very casual network intrusion.
The second red flag for WLAN design and installation is physical security. This involves mounting the access points in such a way that they cannot be stolen, moved, vandalized, blocked, or damaged. It also involves considering coverage areas, and minimization of coverage outside of the area intended to be covered (one would like to cover the building interior, but perhaps not the parking lot, adjacent buildings, or public hallways). This requires structured access point placement and antenna patterns.
Security is clearly a matter of degrees, and the highest network security generally comes at the highest cost (if not in hardware, in administration). But a brief review of the 802.11b authentication process and WEP, and some additional security solutions can let you design suitable levels of security for a WLAN installation.
802.11b factory default settings
WLAN equipment is factory shipped with the authentication configured as "open system." This means that any client adaptor may associate with the access point. Also, WEP is configured in its default condition, which is disabled. All of the data is transmitted such that anybody with an 802.11b client adaptor can read the data. There are no barriers to accessing the network or reading the data. Why was this done? Mainly for simplicity, but there are some applications where it is desirable for anybody to engage an access point. This was envisioned to provide easy access to public access points for free public Internet access, or for ad hoc networks between client adaptors. For most enterprise installations, this convenience is not important.
Many WLAN users do not realize that when they plug an access point into their network, and do not take any other security measures, their network is immediately visible to anyone (within range of the access point) with an 802.11b client adaptor.
The whole world is watching
The basic security features provided by 802.11b are Shared key authentication and WEP enabled. Shared key authentication means the client adaptor must possess a key, which permits it to engage the access point. Without the key, presumably provided by a network administrator, the client adaptor is not permitted to access devices on the network.
But the shared key authentication has proven to be inadequate for most enterprise applications. The key is resident on the client, so if the client is stolen or lost, the key is compromised. Since other clients configured to use the same network have the same key, they must all be re-configured with a new key, which creates a key management problem.
Another problem with shared key authentication is that potentially participating client adaptors must respond correctly to a cryptographic challenge from the access point. The client adaptor decrypts the message using the key and returns it to the access point. If the client uses the correct key to decrypt the message, the access point authenticates the client. But the problem is that the message is transmitted both in its encrypted form and its plain text form, making it relatively easy for a motivated intruder to determine the key and emulate an authorized device.
Enhancing basic security
With WEP enabled, the data payload in every radio packet is encrypted. But the encryption used by WEP can be exploited by downloadable freeware programs. WEP may be a deterrent to casual intruders, but a determined or motivated intruder can fairly quickly authenticate to a network and decrypt data packets, leaving the network fully exposed.
Several vendors support enhanced authentication and encryption algorithms, but these are generally proprietary solutions, meaning that every access point and client adaptor must be from the same vendor. But on the plus side, with some vendors' equipment, a RADIUS server or authentication controller can be used for authentication. This requires the user to provide a user name and password, thereby authenticating the user, not just the device. This avoids the problem of the "compromised" shared key. Use of strong passwords with a RADIUS server or an authentication controller can provide fairly good electronic security. It does, however, require effective administration of user names and passwords.
Fortunately, the IEEE 802.11 committees are aware of the authentication and WEP shortcomings. The 802.1x committee has defined a standard for authentication and key management for Ethernet that should eventually be integrated with the 802.11b systems. And these solutions would be standards-based and not proprietary, so that any vendor's wireless client would work with any vendor's access point.
Just as a Virtual Private Network (VPN) can be used to provide a secure connection across a public Internet, it can also provide a secure connection from the wireless client to the network. The VPN client software resides on the wireless client, and a VPN server authenticates and encrypts transactions between the wireless client and the network. This is generally considered to be a very secure implementation and will work transparently on any vendors' 802.11b equipment. It does require, however, an investment in VPN client software and a VPN server.
null
In addition to considering authentication and encryption security measures, you should also separate the WLAN from the rest of the network with a wireless firewall gateway. The wireless traffic should be outside the enterprise firewall or within the demilitarized zone. Network security policies should be reviewed, and network managers should periodically audit their facilities for rogue 802.11 networks or intrusion attempts.
In addition to the electronic security, make sure to incorporate physical security for the access point locations, based on a site survey that involves assessing desirable access point locations, setting up a temporary access point, and performing signal level and quality measurements around the perimeter. The site survey is essential for providing effective coverage when more than one room is involved, and generally is much more cost-effective than a "wag" on access point quantity and locations. The site survey determines the optimum locations for access points.
Your access points must also be protected from theft, accidental moves, vandalism, damage, or blockage. The requirements to provide effective coverage and simultaneously secure the access points seem to be at odds with each other, since access points can rarely be mounted in a locked telecommunications room and still provide the desired radio coverage. Access points mounted in "public" areas (classrooms, meeting rooms, hallways, airports, lobbies etc.) where they are most needed are candidates for theft, accidental moves, blockage or other mistreatment, causing network downtime, degraded network performance, and voiding RF coverage and manufacturers' warranties, etc.
Nevertheless, your access points must be physically secured, yet still radiate as desired. Consider lockable enclosures that can be wall-mounted or drop ceiling-mounted. You can also connect external antennas to the access point via coaxial cables, or integrate them directly with the enclosure. Lockable enclosures deter theft, vandalism, and accidental moves, and are less likely to be accidentally blocked. The integrated antennas prevent the antenna from being stolen or tampered with.
In addition to security, these enclosures support moves, adds and changes. As access point standards or requirements change, you can swap out the access points, or install additional access points, all the while leaving the data wiring and power wiring in place.
Closing the window on intruders
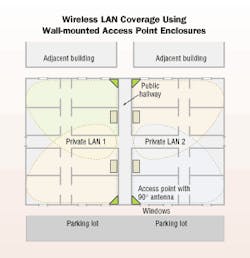
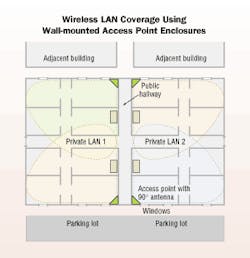
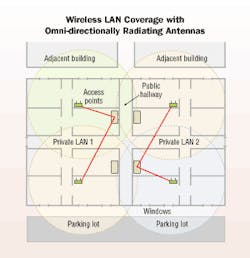
Certain external antennas, such as patch antennas, can create a directive beam that radiates in a specific direction. The figure on page 17 illustrates the advantage of using wall-mounted enclosures with directive beams, versus an access point with an omni-directionally radiating antenna.
The omni-directional antenna (commonly the "rubber duck" dipole antenna with which the access point is shipped) radiates in all directions, regardless of where coverage is required (see figure, this page). This may include out the window, to the parking lot, adjacent buildings, or public hallways. Obviously, you don't want to provide coverage in these areas as it provides an opportunity for an attacker to leisurely examine and probe the network from a car in the parking lot or building across the street.
But by using wall-mounted enclosures with patch (or directive) antennas, you can provide coverage where it is desired, and minimize coverage out the window or to other undesired locales. The 90° beam-width antenna, when mounted in the corner of the room, provides effective coverage in the room and minimizes transmission out the window. Although electronic security measures are still required, providing coverage only where it is desired can help to deter an intruder.
Wall-mounting the access point enclosure also simplifies the task of wiring the access point, since you can run the data wiring along the wall instead of from the closet, across the room, and to the access point location.
Most importantly, when using WLAN equipment, engage the 802.11b standards-based shared key authentication, and enable WEP encryption, available on all Wi-Fi-compliant client adaptors and access points. (Remember, these come shipped with open system authentication and WEP disabled.)
Scott Thompson is president of Oberon Inc., (www.oberlinwireless.com) a value added reseller in the wireless LAN market.