Video surveillance in the digital age
The digital security market faces challenges, sees solutions.
While the topic of security is on the minds of many people today, in both our professional and our private lives, the term "security" is often difficult to define because it is, in a way, all-encompassing. Closed-circuit television (CCTV), access control, biometrics...and the list goes on. Each of these technologies can be considered forms of security, but they are vastly different from each other.
Attempting to address the history, current trends, and future directions of all these technologies would not allow for in-depth discussion of any single area. In this article, I will detail what I call "physical" security, which includes monitoring and surveillance to protect life, limb, and physical property. This monitoring is often coupled with human reinforcement. And the technology involved has been relatively unchanged for decades. I will discuss how and why that technology should change, beginning now.
Traditional video surveillance
Traditionally, video surveillance has consisted of black-and-white, fixed-position cameras, most of which are analog. Their primary application has been incident detection; that is, to document on tape something that has happened. By its nature, it has been a reactive exercise. A fixed video camera set up in a parking lot may record an act of vandalism or an automobile theft, but it won't prevent such an act.
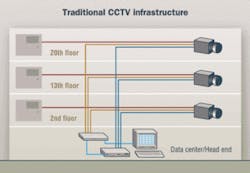
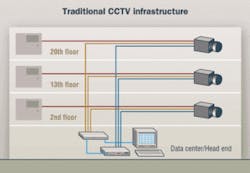
From an infrastructure standpoint, traditional analog CCTV systems have a high total cost of ownership, which includes component acquisition, maintenance, repair, and ongoing manual-labor expenses. The typical CCTV camera set-up requires up to three separate cables per camera—one for power, one for transmission of the video signal, and one for control (pan/tilt/zoom capabilities). Consider also that two of those three cables—the two that carry the video signal and the control commands—must be home-run to a central head end, which could be several floors away.
Adding to this equation is a lack of standards for designing or installing the infrastructure. We in the world of the TIA/EIA-568 standard series are quite accustomed to a set of specifications that allow for product interoperability and define system performance as well as, to a great extent, system set-up. Hence, the term "structured" cabling systems.
No such specifications prevail in the arena of CCTV infrastructure. That fact results in two noticeable consequences: proprietary systems and freewheeling installation practices. Making moves, adds, and changes (MACs) to such proprietary, unstructured infrastructure systems proves costly.
Basically, a survey of the CCTV market today is reminiscent of the computer-networking world of 1989, where an IBM mainframe system included RG-62 cable, the IBM AS/400 used twinax, DEC VAX networks used 50-Ω coaxial cable, and early Ethernet systems were Thicknet and/or Thinnet.
Security market evolution
Three fundamental events are forcing change in the physical-security industry. First, security is changing from reactive to preventative. Concerns over terrorism, specifically over the past two-plus years, have been the primary cause for this shift. Second, non-traditional security applications and technologies are emerging. And the third event causing change in the security world is a rapid shift of security ownership and responsibilities within organizations.
Let's look at these drivers:
- Reactive to preventative. Today, the emphasis is on preventing events from happening in the first place, rather than simply recording them when they do happen. This change requires complex technological advancements, including intelligent systems and pre-event warnings. The notion of "smart" surveillance is a recent introduction to the mindset of many. All in all, this shift requires a different mindset for system designs and implementations.
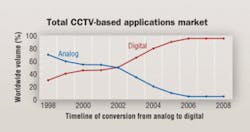
- Non-traditional security applications. Network security no longer is limited to the prevention and detection of hackers. Physical networks are susceptible to internal sabotage, and the need has emerged to monitor a network's physical assets. This requires remote monitoring and surveillance capabilities. A shift from analog to digital technology within CCTV systems is a necessity to achieve such remote monitoring.
- Shift of security "ownership." Physical-security applications that use Internet Protocol (IP) are forcing security into the information-technology (IT) space within organizations. Today, within 40% of all Fortune 1000 companies, the security department reports up to IT. And even those not reporting through IT are forced to learn IP-centric applications (like video over IP) to effectively carry out their objectives. This scenario is similar to the early 1990s "battles" between organizations' telecommunications and LAN groups. Just as that battleground settled into an efficient working system, so too will the current one between physical security and IT.
In fact, the executive position of chief security officer (CSO) has been created in many organizations to oversee both physical and network security. A Booz Allen Hamilton survey of chief executive officers found that 54% of corporations with $1 billion in annual revenue have a CSO. Ninety percent of CSOs have an IT background. And 80% of corporate security budgets come from within the IT budget. Certainly, these indicators point to a significant role on the part of IT in security decisions and operations.
The extent to which security systems are a "turf war" between departments within an organization is reminiscent of networking in the early 1990s. For example, in 1991, printers were the responsibility of an office manager or a facilities department. When a worker needed a new printer or had trouble with an existing one, the call was made to the office manager. Shortly thereafter, printers became part of the network and were shared among several users. Once printers became network nodes, the corporation's IT department took interest in and, more importantly, responsibility for them. Security systems are following that path today. Like printers did more than a decade ago, security systems are shifting from a stand-alone asset to part of an integrated, technology-based network.
As corporate IT departments inherit security systems, they are finding them to be vastly different from the structured, managed voice and data systems they currently administer. Security systems are proprietary in nature, offering limited migration options for digital or IP transmission, difficult and costly to maintain and expand, not subject to industry standards for installation or deployment, and deployed by an installer base that is unfamiliar with IT environments.
Security-system migration faces several significant and sometimes insurmountable barriers. Video-compression technology is still a question mark, as there is no single, definitive compression technology that is universally accepted. The prospect of running surveillance on a network raises questions about bandwidth capability, which in turn raises questions about whether security systems require parallel LANs or can function on shared LANs. There is no seamless migration plan for the security system itself, such as the ability to integrate with future digital needs and future integration with access control.
Bridge to the digital age
After having researched the video surveillance market for several years, with business interests in mind, we believe that a fully functional system, including point-tilt-zoom cameras, does in fact require a parallel system. Such surveillance capabilities demand enough bandwidth that if run on a shared system, the data transmission on that same system would suffer greatly.
Considering that responsibility for video surveillance is steadily shifting to IT departments, an ideal infrastructure is one based on components and architectures that the IT department is familiar with.
In this transition period, as more and more IT departments take on new responsibilities including surveillance and other security measures, all will be challenged to develop efficient, cost-effective and, of course, reliable systems.
Editor's note: This article is derived from a presentation of the same title given by Anixter Inc. (www.anixter.com). The presentation also details Anixter's CCTP - Closed Circuit over Twisted Pair surveillance system.